TEE Framework
In order to aid future developments and to make use of the crate system of rust, we have split the project in 2 repositories:
- The application
- The framework (or tee-base)
What is OPTEE
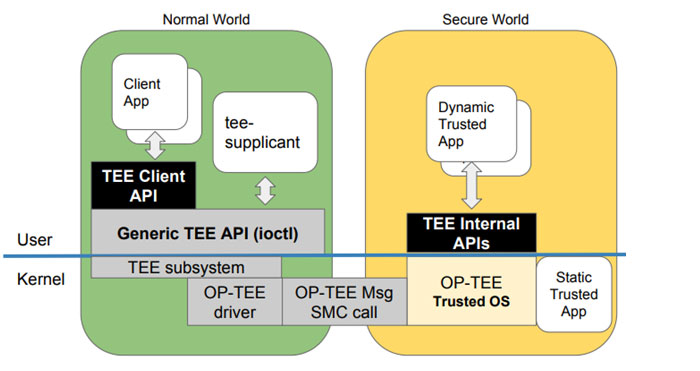
OP-TEE is a Trusted Execution Environment that implements the GlobalPlatform TEE specification. This implementation relies on the Arm TrustZone as the hardware mechanism that isolates a secure environment from the normal world. This isolation comes with different features at the CPU level, like:
- Secure interrupts
- Virtual memory MMU with secure attributes
- Secure code, data and memory
- Trusted boot
- Secure threads
- Trusted File System
These features are not accessibled, modifiable or seen from the normal world where the Operating system is running.
Optee comes with two important APIs, as follows:
-
TEE(Trusted execution environment) whose API is used to interact with the secure world in a controlled manner. This API is used by user code(Trusted Application or better known as TA) that runs "inside" the TrustZone. The TA has the following characteristics:
- It is identified by a UUID
- It is isolated from the OS and has access to certain peripherals that the normal OS cannot access (i.e. cryptographic co-processor, etc. )
- It is limited by memory boundaries and the number of available syscalls. These syscalls have to go through the secure environment as a result, normal syscalls for memory allocation, file systems and non-secure peripherals(including networking) are disabled.
-
REE Rich execution environment does not have any limitation in regard to access to networking, memory and peripherals. The API is used to create client instances that open the door to the secure world through a sort of channel communication.
Both APIs are defined by the GlobalPlatform TEE specification.
For more details on how these APIs are used, check our hello-Rustee program
What is tee-base ?
In short tee-base is a rust tee application bootstrapping framework.
What does this mean in practice is that the repository hosts 4 main components:
-
Rust crates with utilities and bindings to the OPTEE API
-
C projects that act as "trampolines" for the rust applications
-
CI testing scripts
This allows the CI worker to execute the script after setting up the environment, so the script will take care of listening for the test outputs and generate a simple report for the CI job.
- A template for new apps
This can be used to set a new project up with the required structure to use tee-base.
We make use this structure in both the project and the example hello world app.
What are these rust crates?
The rust crates present in the framework can be divided in 2:
-
The
zondee-teeccrate for the host application -
The
zondee-uteecrate for the trusted application
zondee-teec
This crate provides abstractions and utilities to interact with the OS's OPTEE API, so that it's possible to more idiomatically create sessions and interface with the trusted application, like invoking commands in a much more ergonomic way compared to the raw C bindings, which are still accessible through the crate.
zondee-utee
This crate is the counterpart to zondee-teec, providing abstractions and utilities to interact with the OS's OPTEE API but from the TEE (trusted execution environment).
Among other things, this also means providing bindings to the official panicking function.
Other features include:
-
A
GlobalAllocatorto make use of dynamic allocation via the official OPTEE allocation API -
A
CryptoRngimplementation making use of the official OPTEE randeom generation API -
A
Logimplementation to allow use of thelogcrate and custom log handlers